Domain-based Message Authentication, Reporting & Conformance (DMARC)
Email DNSWhen an email is sent or received, there is no clear indication that the email is authentic or if it was sent from a validated sender address or domain. One way to improve email security is the DMARC standard.

DMARC allows senders to instruct email providers on how to handle unauthenticated mail via a DMARC policy, removing any guesswork on how they should handle messages that fail DMARC authentication. DMARC protects email from spoofing, phishing and spamming.
DMARC builds on the commonly-deployed Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) protocols. A policy for DMARC allows a sender domain to specify if its email uses SPF and/or DKIM. Policies can be set for sending email to a spam folder or reject it if the authentication methods fail. If an email recipient gets an email that fails these authentications, they also have an option to report it back to the sending domain.
So, DMARC adds an important function of reporting. When a domain owner publishes a DMARC record into their DNS record, they get insights into who is sending email on behalf of their domain.
DMARC Record
DMARC policies are published in the DNS as Text (TXT) record and announce what an email receiver should do with non-aligned mail it receives. For example,
"v=DMARC1;p=reject;pct=100;rua=mailto:postmaster@dmarcdomain.com"
In this example, the sender requests that the receiver reject all non-aligned messages and send a report about the rejections to a specified address.
DMARC Policies
There are three possible DMARC policies:
- none (monitoring only)
- quarantine
- reject
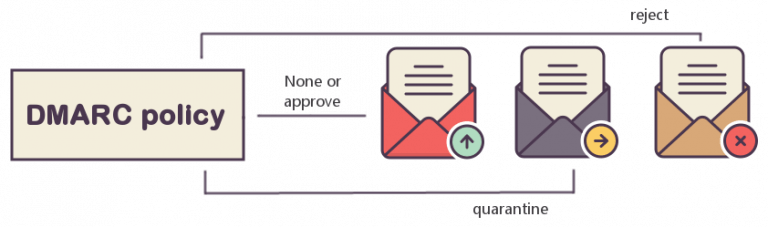
1. p=none
It instructs email receivers to send DMARC reports to the address published in the RUA or RUF tag of the DMARC record. This is known as a monitoring only policy because you gain insight in your email channel. It does not instruct email receivers to handle emails failing the DMARC checks and it will not affect the deliverability.
2. p=quarantine
Besides sending DMARC reports, it instructs email receivers to put emails failing the DMARC checks in the spam folder of the receiver. Emails that pass the DMARC checks will be delivered in the primary inbox of the receiver. The quarantine policy will mitigate the impact of spoofing, but spoof emails will still be delivered to the receiver in the spam folder.
3. p=reject
Besides sending DMARC reports, it instructs email receivers to not deliver emails failing the DMARC checks. Emails that pass the DMARC checks will be delivered in the primary inbox of the receiver.
DMARC Reports
There are two types of DMARC reports:
- Aggregate Reports (RUA)
- Forensic Reports (RUF)
Aggregate Reports (RUA): Sent on a daily basis, it provides an overview of email traffic. It includes all IP addresses that have attempted to transmit email to a receiver using your domain name.
Forensic Reports (RUF): Sent real time only for failures, it includes original message headers. It may also include original message.
History of DMARC
The DMARC standard was first published in 2012 to prevent email abuse. DMARC was created by PayPal together with Google, Microsoft and Yahoo. DMARC is originally developed as an email security protocol. At first, it was mostly adopted by security experts in the financial industry.
Originally, the email authentication techniques DKIM and SPF helped to protect domains from scams. However, these security measures can be bypassed. In order to fully secure your domain and email channel, DMARC creates a link between SPF an DKIM.